Data Armor
DataArmor is a Zero Trust encryption and extortion-prevention platform which is location aware and has carrier detect abilities. This platform enables zero trust encryption across mobile devices, and public or private clouds. It enables organizations to fully own and control their encryption keys, ensuring data remains secure, recoverable, and unreadable to attackers—even in the event of ransomware or insider threats.
Get started today



.png)
Key features
Extortion Prevention Platform
Enterprise-wide key management platform using Symmetric cryptography keys
Schedule a demo
Why Choose DataArmor?
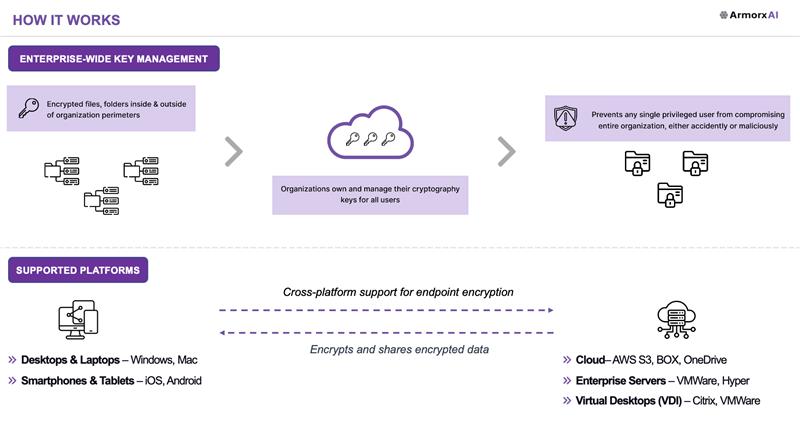
Organization-Owned Keys
Organizations own and manage their cryptography keys for all users. Never compromise control of your security infrastructure.
.png)
Privileged User Protection
Prevent any single privileged user from compromising the entire organization, whether accidental or malicious.
.png)
Perimeter-Aware Protection
Location-aware and carrier-detect technology protects files and folders inside and outside organizational boundaries.
DataArmor safe guards vital assets
- Enterprise-wide encryption key management platform
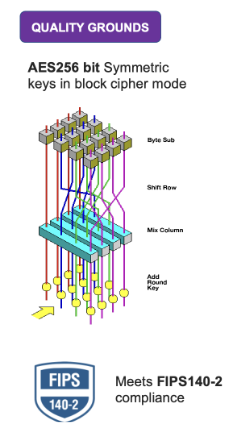
- AES256 bit Symmetric keys in block cipher mode
- Meets FIPS140-2 compliance
- Deployed on-prem or in AWS/Azure Clouds (Support for GCP in Q3)
- AES256 bit Symmetric keys in block cipher mode
- Meets FIPS140-2 compliance
- Deployed on-prem or in AWS/Azure Clouds (Support for GCP in Q3)
Schedule a demo
How it works
Endpoints, Mobile, Public/Private Cloud Data Protection
Cloud Agnostic
61% of organizations use more than one public cloud provider.
Key Management
Keys are served in real-time and one unique key is assigned to each fil and folder resulting in stronger security
True end-to-end Encrypted File Sharing
Unique keys allow users to share individual files across any public or private cloud.
Carrier Detect
Platform automatically prevents carrier hopping and locks container when violation occurs
Secure Vault
Created on endpoints, private clouds and public clouds where all encrypted files and folders reside.
Location Aware
Platform only works in defines of pre-determined location
Challenges
ArmorxAI Assurance
Recover all your data on endpoints
Ensure that any data which cybercriminals copied will be unreadable
Don't pay any ransom
- Operates as an independent layer on endpoints and mobile devices
- Complements existing full-disk encryption solutions
- Provides encryption while the devices are on and connected to the Internet – this enables employees to travel with their company issued devices WITHOUT fear of losing data from those devices
Schedule a demo
.png)

.png)
.png)

.png)
